The S-DES encryption algorithm takes an 8-bit block of plaintext and a 10-bit key as input and produces an 8-bit block of ciphertext as output. The S-DES decryption algorithm takes an 8-bit block of ciphertext and the same 10-bit key used to produce that ciphertext as input and produces the original 8-bit block of plaintext.
- Sdes P10 And P8 Key Generation Manual
- Sdes P10 And P8 Key Generation 8gb
- Sdes P10 And P8 Key Generation System
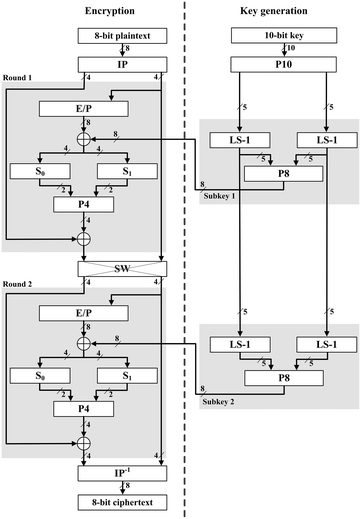
The encryption algorithm involves five functions: an initial permutation (IP); a complex function labeled fK, which involves both permutation and substitution operations and depends on a key input; a simple permutation function that switches (SW) the two halves of the data; the function fK again; and finally a permutation function that is the inverse of the initial permutation (IP–1).
Key Generation P10 P8 P8 LS-1 LS-1 LS-2 LS-2 8 8 5 5 5 5 5 5 K1 K2 10. P10 Permutation k1 k2 k3 k4 k5 k6 k7 k8 k9 k10 k3 k5 k2 k7 k4 k10 k1 k9 k8 k6.
P10 10-bit key 8-bit plaintext ENCRYPTION DECRYPTION 8-bit ciphertext 8-bit ciphertext Figure C.1 Simplified DES Scheme 8-bit plaintext Shift P8 Shift P8 fK K1 K2 K2 K1 SW IP–1 IP fK fK SW IP IP-1 fK P10 10-bit key P8 K1 P8 LS-1 LS-1 LS-2 LS-2 K2 5 10 5 5 8 8 5 5 5 Figure C.2 Key Generation for Simplified DES IP 8-bit plaintext 8-bit. CodeProject, 20 Bay Street, 11th Floor Toronto, Ontario, Canada M5J 2N8 +1 (416) 849-8900.
1.3: In addition, Apple's Bootcamp drivers for AMD and NVIDIA graphics cards are often outdated, and Lumion 6.5 and newer might not be able to start on a Mac with those drivers. Please verify that you can install the latest official NVIDIA or AMD driver from the AMD or NVIDIA websites before running Lumion on your Mac. Lumion for mac.
We can concisely express the encryption algorithm as a composition1 of functions.
This is a program for Encryption and Decryption with Modifies & Simplified DES. This Algo takes 8-bits of plaintext at a time and produces 8-bits of ciphertext. It uses 10-bits of key for Encryption and Decryption.
Global Variables
Original S-Box
Modified S-Box
Selection of Function for Original and Modified S-Box
We now describe the mapping F. The input is a 4-bit number (n1n2n3n4). The first operation is an expansion/permutation operation:
Hp laserjet 1060 driver for windows 7. HP ePrint software – HP ePrint software provides the ability to wirelessly print from a Windows or Mac desktop or laptop, to any wireless direct printer that is ePrint-enabled and connected to a network or HP cloud, from within applications using the standard File Print method. Includes a driver for Windows and a.pdf workflow for Mac. Download HP printer drivers or install DriverPack Solution software for driver scan and update. HP LaserJet 1020. HP LaserJet M1005 MFP. Windows XP, 7, 8, 8.1. Download the latest drivers, firmware, and software for your HP LaserJet 1020 Printer.This is HP's official website that will help automatically detect and download the correct drivers free of cost for your HP Computing and Printing products for Windows and Mac operating system.
E/P = (4, 1, 2, 3, 2, 3, 4, 1)
The first 4 bits (first row of the preceding matrix) are fed into the S-box S0 to produce a 2- bit output, and the remaining 4 bits (second row) are fed into S1 to produce another 2-bit output.
Autocad mechanical tutorial pdf. These two boxes are defined as follows:
The S-boxes operate as follows. The first and fourth input bits are treated as a 2-bit number that specify a row of the S-box, and the second and third input bits specify a column of the Sbox. The entry in that row and column, in base 2, is the 2-bit output.
Next, the 4 bits produced by S0 and S1 undergo a further permutation as follows:
P = (4, 2, 4, 3, 1)
The output of P4 is the output of the function F.
Shifting of Keys
Key Generator
A 10-bit key shared between sender and receiver. From this key, two 8-bit subkeys are produced for use in particular stages of the encryption and decryption algorithm.
First, permute the key in the following fashion. Let the 10-bit key be designated as (k1, k2, k3, k4, k5, k6, k7, k8, k9, k10). Then the permutation P10 is defined as:
P10 (k1, k2, k3, k4, k5, k6, k7, k8, k9, k10) = (k3, k5, k2, k7, k4, k10, k1, k9, k8, k6)
P10 = (3, 5, 2, 7, 4, 10, 1, 9, 8, 6)

Next we apply P8, which picks out and permutes 8 of the 10 bits according to the following rule:
P8 = (6, 3, 7, 4, 8, 5, 10, 9) https://cyccontpahi1976.mystrikingly.com/blog/download-game-nascar-rumble-racing-cso.
Sdes P10 And P8 Key Generation Manual
Next we apply P8, which picks out and permutes 8 of the 10 bits according to the following rule:
P8 = (6, 3, 7, 4, 8, 5, 10, 9) https://cyccontpahi1976.mystrikingly.com/blog/download-game-nascar-rumble-racing-cso.
Sdes P10 And P8 Key Generation Manual
We then go back to the pair of 5-bit strings produced by the two LS-1 functions and perform a circular left shift of 2 bit positions on each string.
Sdes P10 And P8 Key Generation 8gb
Finally, P8 is applied again to produce K2.
Encryption and Decryption
The input to the algorithm is an 8-bit block of plaintext, which we first permute using the IP function:
IP = (2, 6, 3, 1, 4, 8, 5, 7)
This retains all 8 bits of the plaintext but mixes them up. At the end of the algorithm, the inverse permutation is used:
IP–1 = (4, 1, 3, 5, 7, 2, 8, 6)
The Switch Function
The function fK only alters the leftmost 4 bits of the input. The switch function (SW) interchanges the left and right 4 bits so that the second instance of fK operates on a different 4 bits. In this second instance, the E/P, S0, S1, and P4 functions are the same. The key input is K2.
